How to create a shared photo library with Lychee
By Ovidiu Pacuraru - 13 Jun 2016
Today’s blog post comes from guest writer Ovidiu Pacuraru.
In this tutorial, we will show you how a family on holiday can organize images from dad’s DSLR, mom’s iPhone and the kid’s Android phone inside one album. They can all use the same Lychee grain in Sandstorm from a web browser; this tutorial shows how to set it up.
There are at least a couple of different scenarios where you’d want to create a photo library and share it with others. Another example is when 3 people are writing a blog but only one editor approves images, so images need to be collected at a central point. I have found uploading and sharing via Google to be a bit hit and miss.
In any case where you need to create a shared photo library using Lychee, you can follow these steps:
1. Get Sandstorm by signing up for Oasis or installing it on your own machine.
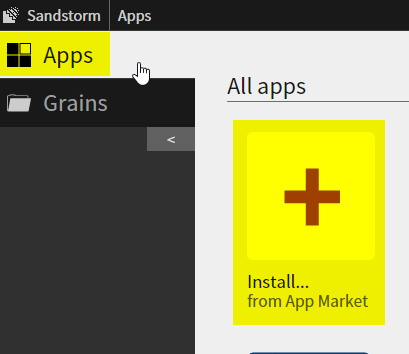
2. Install Lychee from the App Market
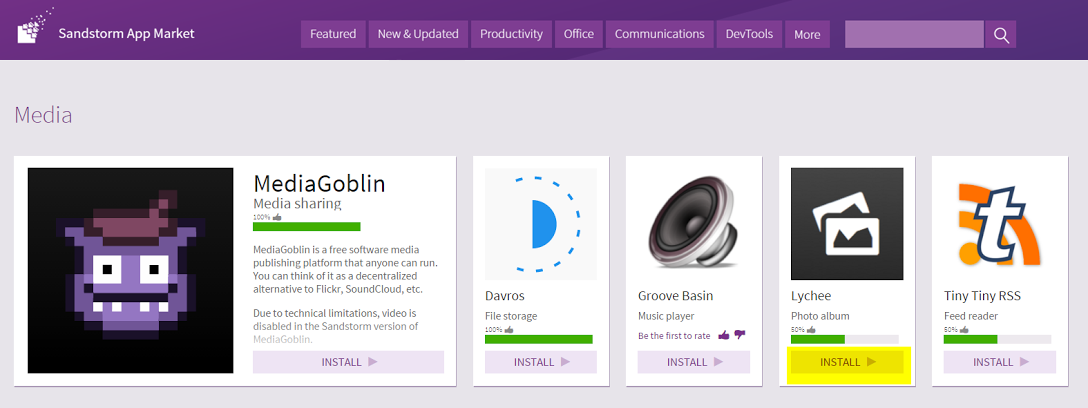
3. In the next window that opens, click: INSTALL
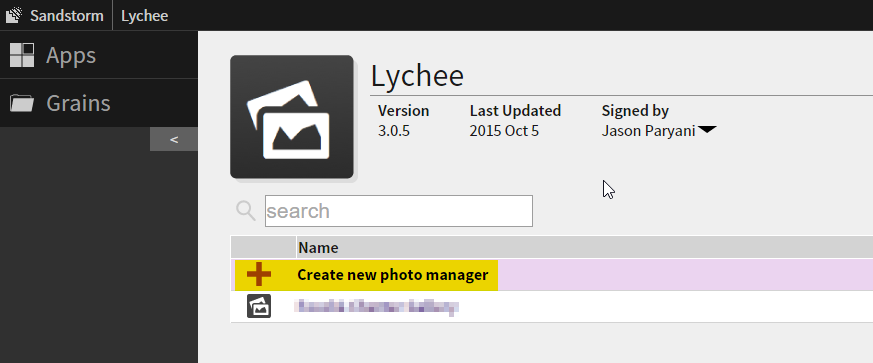
4. Create a new grain
5. Rename your grain
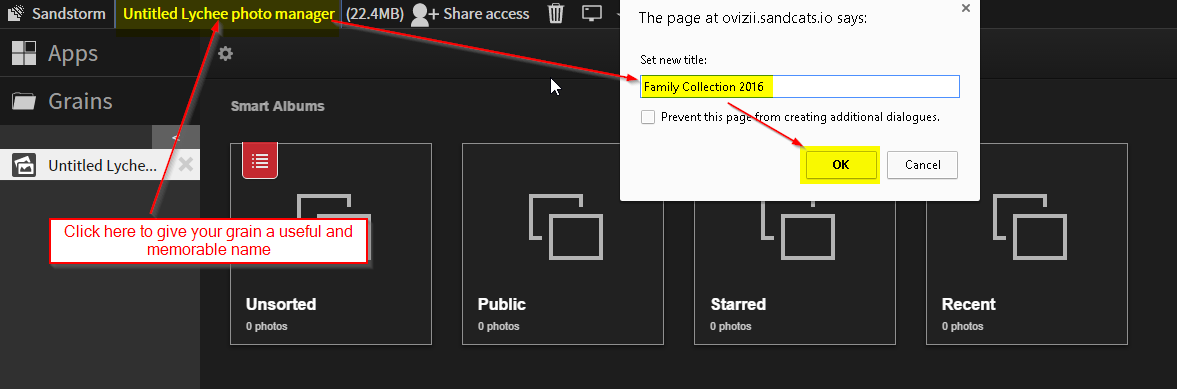
6. Add an album
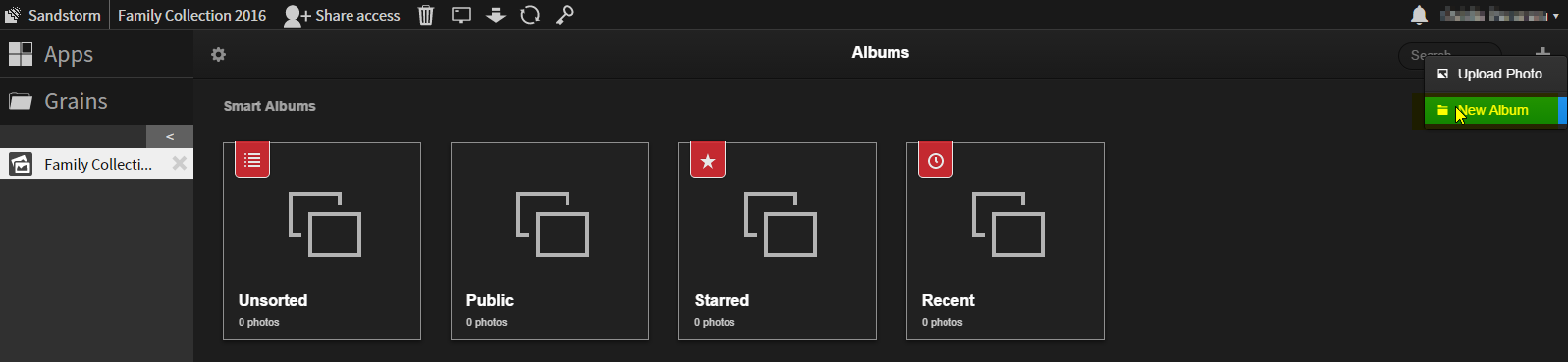
7. Name your album
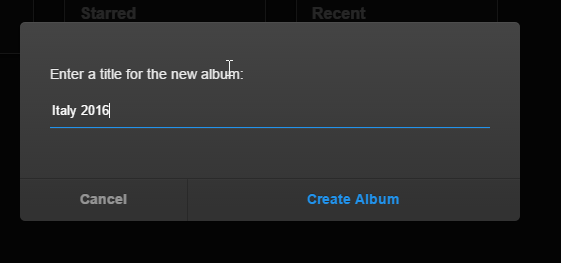
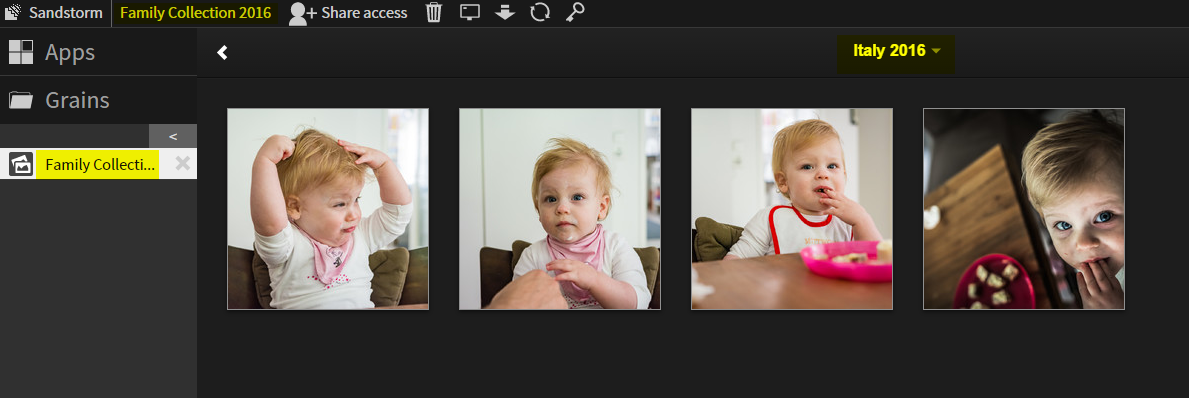
8. Upload some images
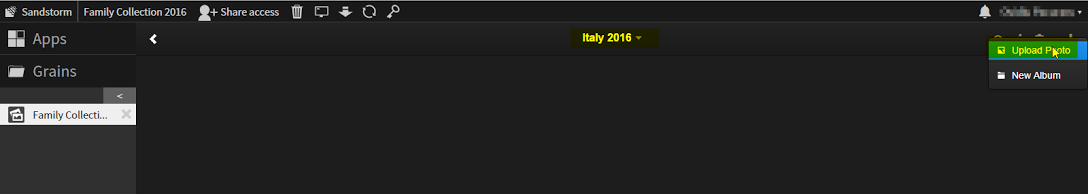
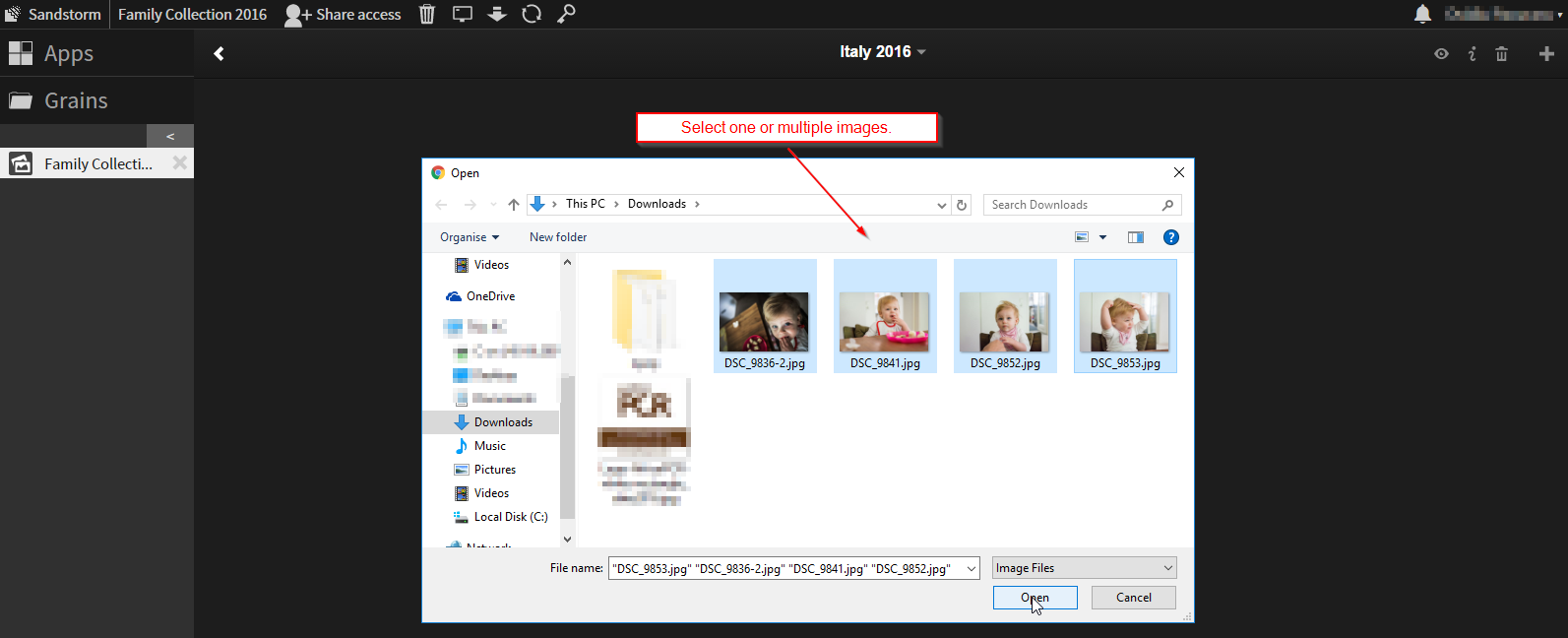
9. Browse your album

10. Share access with your family
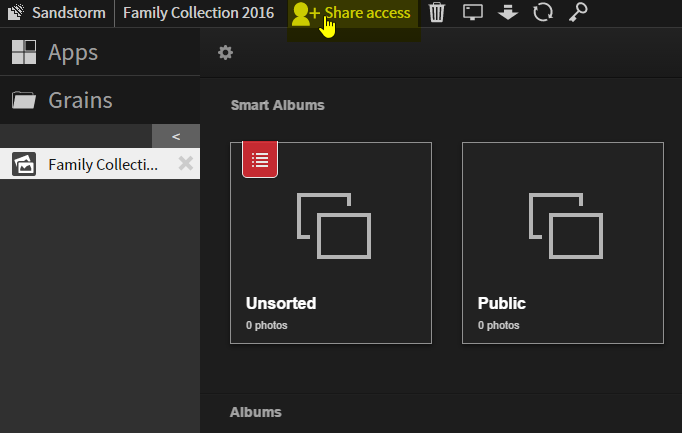
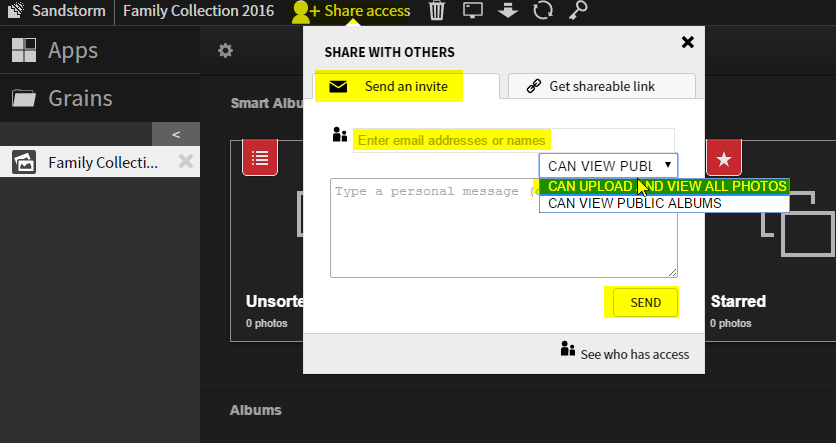
11. Invite family members
2. Install Lychee from the App Market

3. In the next window that opens, click: INSTALL

4. Create a new grain

5. Rename your grain

6. Add an album

7. Name your album

8. Upload some images


9. Browse your album

10. Share access with your family

11. Invite family members

I hope you enjoy creating photo albums using Lychee from the Sandstorm App Market. Don't forget to leave a review!
Upcoming events in June in San Francisco, Morgantown
By Jade Wang - 06 Jun 2016

Designing secure systems with Object-Capabilities, Python, and Cap’n Proto (San Francisco, CA)
Join us for a talk from Sandstorm core dev Drew Fisher about an object-oriented programming inspired technique for designing secure systems called object-capability security. Drew’s talk will be followed by a Q&A session with opportunities to chat with Sandstorm’s community before and after. A huge shoutout and thanks to ThoughtWorks for hosting the meetup and for dinner!
Thursday, June 16, 2016
6:00 PM to 9:30 PM
ThoughtWorks
814 Mission St, 5th Floor, San Francisco, CA
RSVP here: http://www.meetup.com/Sandstorm-SF-Bay-Area/events/231065150/
Building a decentralized web with Sandstorm
If you’re in Morgantown, West Virginia, join the Linux User Group, and meet Sandstorm core dev David Renshaw! David will give an overview of Sandstorm, and will dive into some of the technical details of what makes Sandstorm tick.
Thursday, June 9, 2016
7:00 PM
Listhub
453 Suncrest Towne Centre, 2nd Floor, Morgantown, WV
RSVP here: http://www.meetup.com/Morgantown-Linux-User-Group/events/228038429/
May changelog - what's new in Sandstorm
By Asheesh Laroia - 31 May 2016
This month features a big change: when you delete grains, they are sent to a “Trash” area, where they are held for 30 days before being deleted permanently. I personally have clicked “Delete” on the wrong grain by accident, so I’m very happy with the new feature! This way, I can undo it.
Self-hosters will also appreciate the totally-redesigned admin interface. Visit /admin on your server and you’ll see that it’s easier to navigate and visually cleaner.
Here’s the full changelog. As always, you can visit your Sandstorm server and find the changelog under the “About Sandstorm” section.
v0.164 (2016-05-20)
- Self-hosting: The admin settings UI has been completely revamped.
- Fixed grain debug log auto-scrolling.
- Sandcats: Fixed obscure ASN.1 type issue in CSRs that was causing Globalsign API to complain.
- Fixed bug where logging in via Google or Github while viewing a sharing link which you had already redeemed previously would lead to an error.
v0.163 (2016-05-15) [bugfixes]
- Fixed subtle bug introduced in 0.162 which caused shared grains to refresh every minute.
v0.162 (2016-05-14)
- Implemented “trash”. Deleted grains go to the trash where they can be recovered for up to 30 days.
- Grains can now be deleted from the grain list, without opening them first. Multiple grains can be selected for deletion at once.
- An app can now request that the “who has access” dialog be displayed.
- Fixed bug where after an upload failed, future uploads would show the same error despite not having failed.
- Tweaked the “logout other sessions” button to give better feedback that the request is in-progress.
- When visiting a Sandstorm server that hasn’t been set up yet, you’ll now be redirected to the setup wizard.
- The API endpoint now allows the authorization token to be specified as part of the path, for cases where setting the
Authorizationheader is not possible (especially cross-origin WebSocket).
Case Study: Sandstorm for journalists
By Jade Wang - 23 May 2016
Jason Hernandez is a journalist who often covers sensitive topics like mass surveillance for the North Star Post. And given the nature of his work, he and his colleagues are justifiably concerned about the information security, not just between journalists and sources, but also drafts and storage of source materials. So, when Jason was visiting the SF Bay Area, he dropped by Sandstorm meetup to talk about the Sandstorm server he set up so he and his colleagues so that they can still enjoy the benefits of web applications, like real-time collaboration, while keeping control over their data.
Lightning Talk: Jason Hernandez talks about how North Star Post uses Sandstorm
Are you using Sandstorm for your work? I’d love to hear more about how you’re using Sandstorm and share your story. Drop me a line at [email protected] and tell me about it!
Are you in the Bay Area? Hope you can make it to the next Sandstorm meetup: RSVP here
Or share your Sandstorm use case at local meetups in: Boston, New York, Berlin, Zurich, or Wellington.
Richard Caceres talks about designing open source apps
By Nena Nguyen - 16 May 2016
We had the pleasure of having designer, developer, and app author Richard Caceres speak at our Sandstorm.io meetup in San Francisco on March 24, 2016.
In his talk Richard emphasized the value of free and open source software, he shared design principles that app authors should follow (to create a more cohesive user experience across apps), and he also demoed a newly updated version of his TextEditor app.
“Every app would benefit from allowing you to customize the CSS. I think that’s really important. In TextEditor, you can do that now.”
Watch Richard's full talk to hear more about:
- What makes good free software
- Why you should develop apps for Sandstorm
- The importance of design for apps
- Examples of successful open source design
- Visual guidelines for apps
- New TextEditor features (like customizable CSS)
- And more!
You can follow the slides here:
As a follow-up to his talk, Richard has also recently announced x-gui, a library of web components for building consistent web apps.
Try out TextEditor for yourself and don’t forget to leave a review!